Level Goal
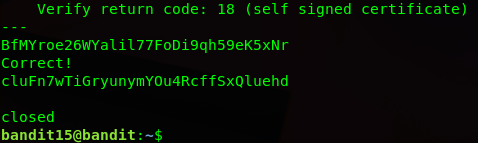
The password for the next level can be retrieved by submitting the password of the current level to port 30001 on localhost using SSL encryption.
Helpful note: Getting “HEARTBEATING” and “Read R BLOCK”? Use -ign_eof and read the “CONNECTED COMMANDS” section in the manpage. Next to ‘R’ and ‘Q’, the ‘B’ command also works in this version of that command…
For this we will use open ssl.
I was not super familiar with this command, so I checked the man pages (best thing ever)
s_client will let us establish a connection, which is exactly what we need.
s_client will let us establish a connection, which is exactly what we need.

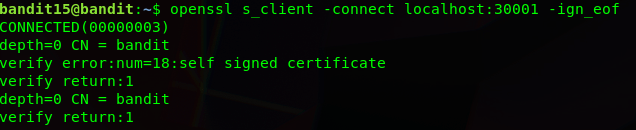
So now we will use openssl with the s_client flag to connect to port 30001 on the server.

[super long openssl output]
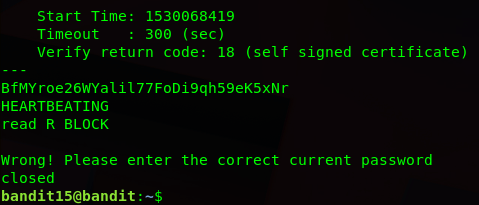
Hmm… looks like we got that error the hint talked about… let’s try adding that -ign_eof param to the end of our command
 [super long openssl output]
[super long openssl output]