Detecting a log4shell exploit against VMware Horizon using CheckPoint Harmony Endpoint
It’s just another day in the SOC world. You wake up, start going about your day, and then BOOM, you get an alert that an abnormal script was run on a VMware box.
After a quick look at the logs, you know that you aren’t getting anything else done today… or are you?
The first thing we notice is cmd being launched by “NoLogonUser” so something launched the command prompt that was not directly user initiated.
This is expected if a script is launched from a process, but tomcat should most likely not be launching cmd.exe, so the behavior definitely stands out as suspicious to me.

If we continue with expanding this detection, we can see CheckPoint prevented this execution, but we want to go deeper. What happened? Why did it happen? How do we prevent it?
Luckily we should be able to answer all of these questions rather easily.
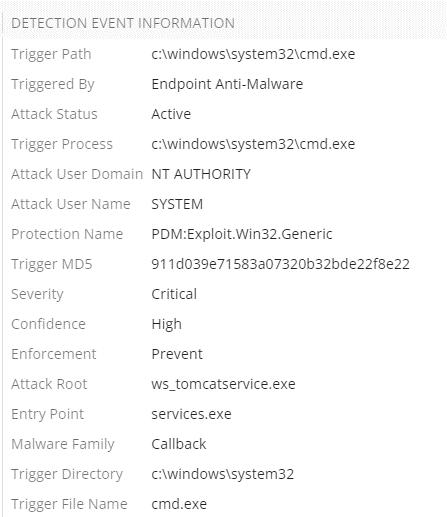
Screenshot showing that cmd.exe was prevented by CheckPoint Harmony Endpoint
Next, we will open up the full forensic report so we get some more information about this attack.
From the report, we navigate to the tree view for a high level overview of the process chain. We can drill into any of these items and gain some additional details for each process.

Here we can see tomcat launching cmd and then cmd launching powershell. This is what we observed earlier as well, just a bit more laid out.
Digging into cmd, we can see the command used to launch powershell, along with the encoded command.
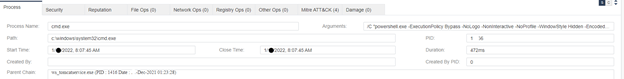
One nice thing about Harmony Endpoint is the ability to decode Base64 data in the app.


It looks like we have our first few IOCs – 72[.]46.52.135 and mad_micky.bat
This post is being written a bit after the fact but if we search that IOC on Virus Total, we see others have also seen is hit Horizon Servers and we have the same Mac_Micky.bat reference.

So, we had a payload reach out to a website and download a second stage.
Once the second payload is seen by Harmony, the processes are killed.
At this point, we know not everything is on fire. Harmony successfully blocked the exploit and gave us some IOCs to look for through the environment; the main action is to get Horizon patched.
Time permitting, it would be nice to launch these scripts in a sandbox and reverse what exactly they are doing, but unfortunately that is not something I am able to do right now.
I am sure some amazing malware analysts will rip this thing apart and expose all the inner workings, and I look forward to reading about it.

DU BIST BLOGGER JETZT
LikeLike