
*This writeup is notes only at the moment*
In the provided zip, we have a couple different files.
We will start by running a quick search with Chainsaw to find any low hanging fruit that may be beneficial later
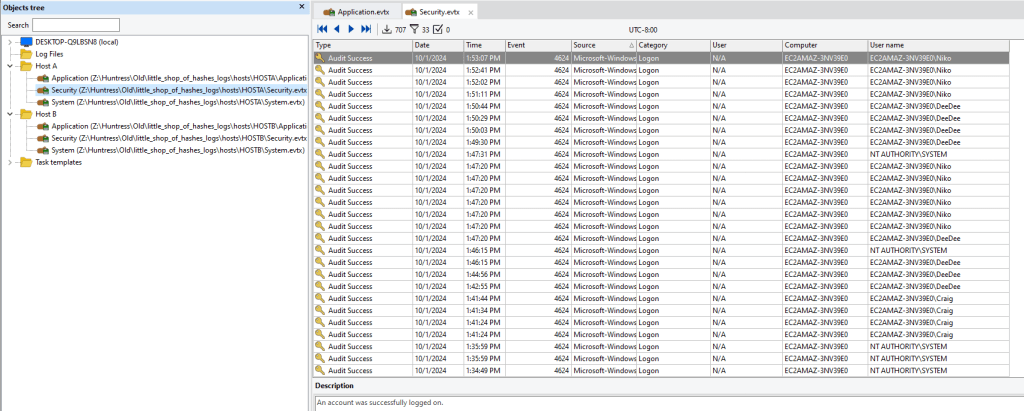
We can also see a lot of failed login activity leading up to a successful sign in. This indicates a probable brute force attack.

1: Are you able to unravel the attack chain? The first question is:
What is the name of the service that the attacker ran and stopped, which dumped hashes on the first compromised host?
If we look through the System logs for Host B, we can see Remote Registry being started and stopped

Answer: Remote Registry
2. What lateral movement technique did the threat actor use to move to the other machine?
Looking at the successful logons, we can see the logon type of 3. This is indicating that the login is remote, likely making this a pass the hash attack.

Answer: Pass the Hash
3: What is the full path of the binary that the threat actor used to access the privileges of a different user with explicit credentials?
In our chainsaw hunting, we can see the following log that shows the binary path
Answer: C:\Users\DeeDee\Documents\runasc.exe
4: How many accounts were compromised by the threat actor?
We can see 3 different user accounts that appear to have been compromised

Compromised Users: Niko, DeeDee, and Craig
Answer: 3
5: What is the full path of the binary that was used to attempt a callback to the threat actor’s machine?
In the application logs for Host A, we can see a lot of attempts to launch nc.exe from DeeDee’s documents folder
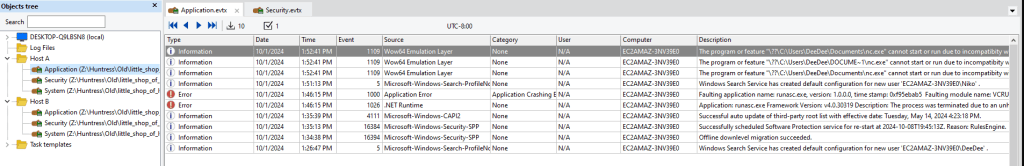
Answer: C:\Users\DeeDee\Documents\nc.exe
