In this challenge, we simply have an obfuscated powershell script.

There are two ways to do this, the manual way and the yolo way…
Reading through this code we can see nothing actually executes until the final line of code where everything is piped and called (ref: https://ss64.com/ps/call.html)
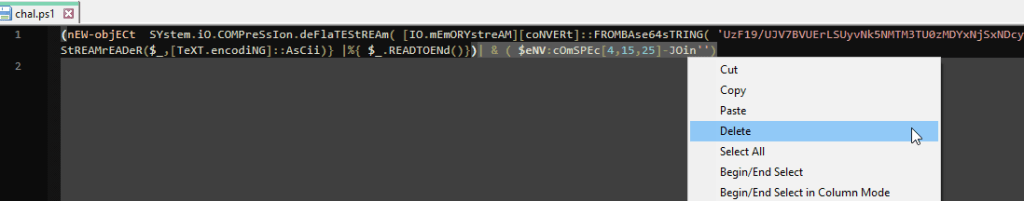
If we simply remove the portion of the script that exceutes the code and save the output to variable, we can then read that variable and get the flag.
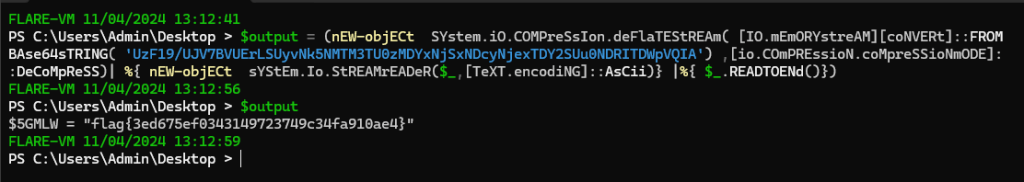
flag{3ed675ef0343149723749c34fa910ae4}
Now, if you are not 100% sure that nothing else in the script will execute, do NOT do this.
The manual way is to decode and decompress the given string, you can use powershell or something like cyberchef to do this.
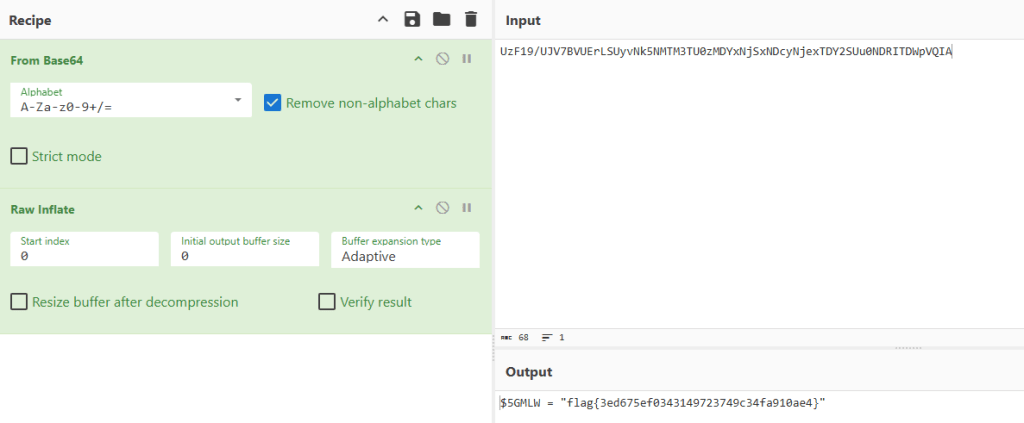
This is by far the safest way to do things.
