This challenge is using ADS and sysmon, two of my favorite things. I loved this challenge!
When we extract this challenge, we have a windows event log using sysmon
We can look for Look for streams being created by filtering down to sysmon event ID 15
Ref: https://isc.sans.edu/diary/26292
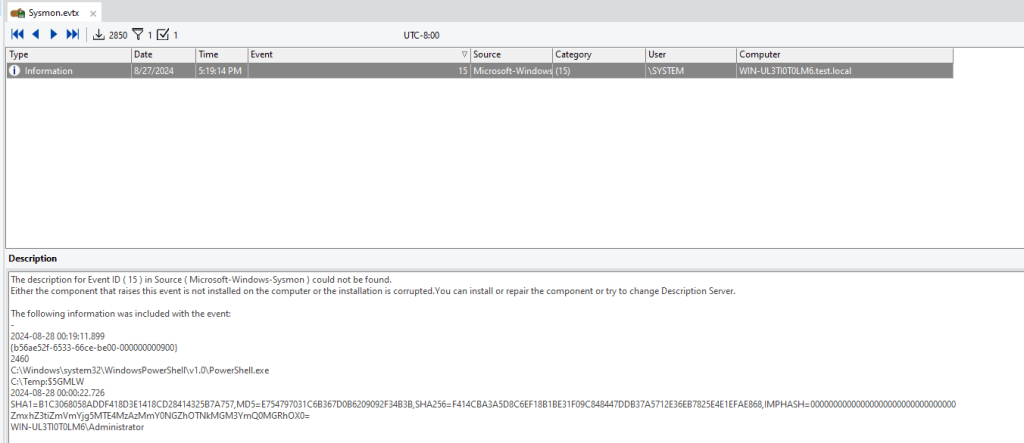
We find what appears to be a base64 encoded string.
Optional: If we want to have the event descriptions for sysmon, we can easily add this by downloading sysmon (https://learn.microsoft.com/en-us/sysinternals/downloads/sysmon) and installing the sysmon manifest
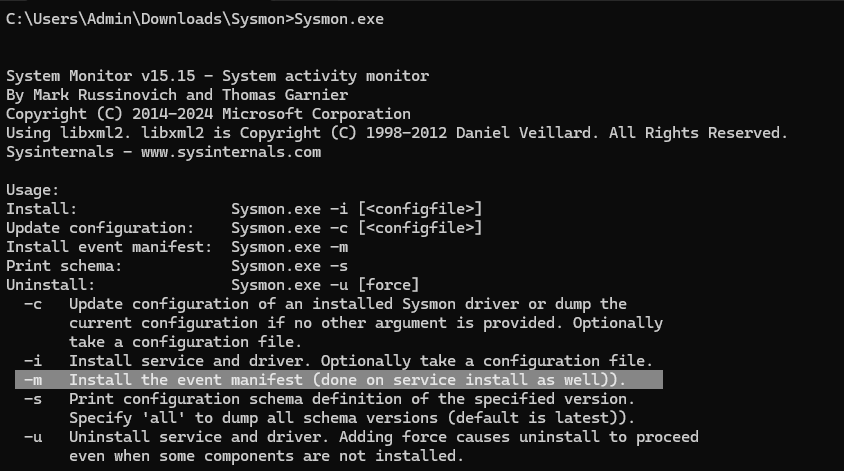
sysmon -m
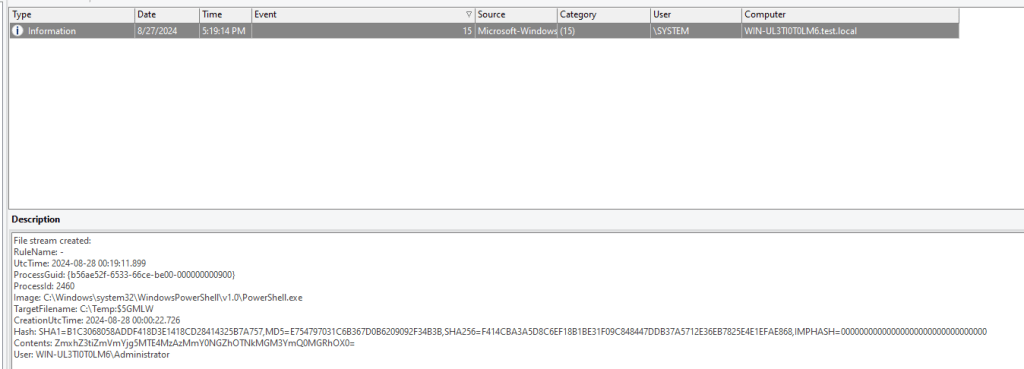
Now if we look at this log, we can see the actual information and have the base64 encoded string in the contents field.
Next we will decode the base64 encoded string
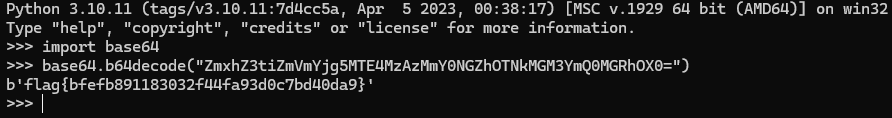
flag{bfefb891183032f44fa93d0c7bd40da9}
